IB Computer Science Practice Java Evaluation 6
IB Computer Science Question 1
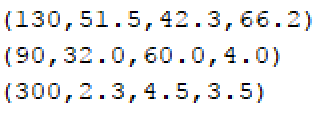
Your task is to find the center of gravity in a system of planets in an alien solar system. To accomplish this task you will need to know the mass of each planet and their coordinates in Three Dimensional Space. This information will be represented in an ordered 4-tuple (mass,x,y,z). All the input data are integers.
For Example, if you were given the following 3 masses, you would calculate the center of gravity in 3 Dimensional Space as follows
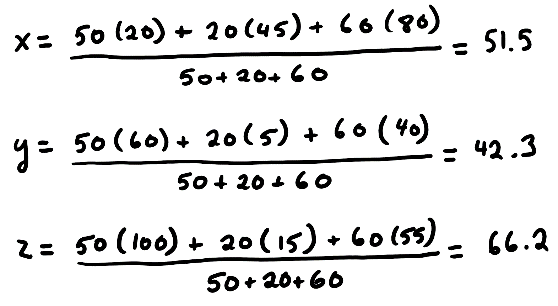
I will be testing your program using a file
- The first line will represent the number of solar systems in the Universe.
- The remaining lines will have (all on the same line)
o A number to represent the number of masses in the solar system followed by the ordered 4-tuples (mass,x,y,z). Everything separated by a space. - There will never be more than 10 masses in a solar system.
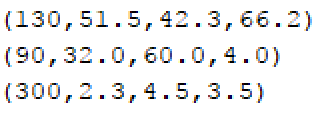
I will expect the output to be to a text file with all the 4-tuple’s of each solar system, each on a separate line. Output the coordinates to 1 decimal spot
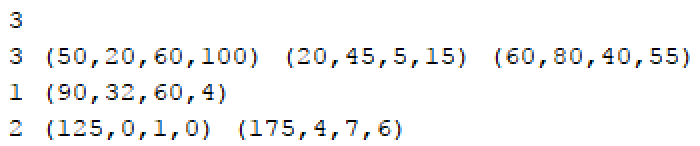
IB Computer Science Question 2
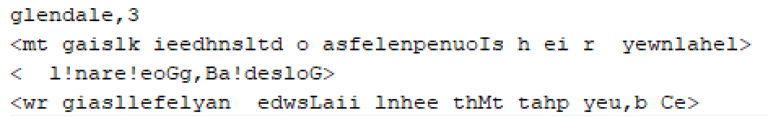
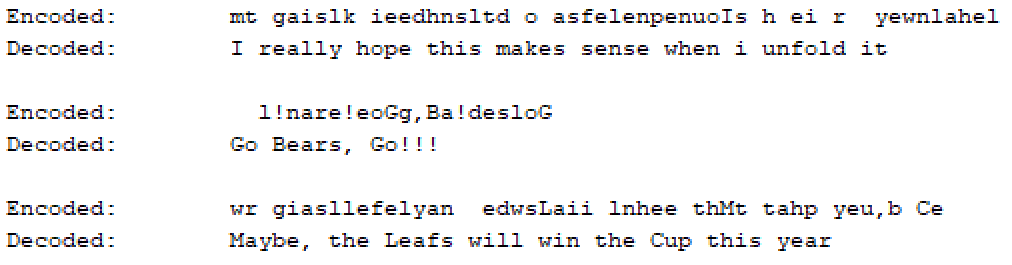
You are an Imperial Spy and have managed to steal some very valuable information from the Rebel Alliance. You have managed to steal both an encrypted message and its decoded equivalent. Unfortunately for the Rebel Alliance, they used a simple one to one code map to encrypt their messages. That means that each letter in the message was substituted for a different letter for the encryption. Simply comparing the two messages together you can see what letter was substituted. This will allow you to decode any other messages they send.
For example, if this is what you stole:
You know that every ‘A’ in the encrypted message is really supposed to be a ‘T’ and that every ‘W’ in the encrypted message is really supposed to be a ‘O‘.
You could use this information to take any encrypted message and print out the decoded message
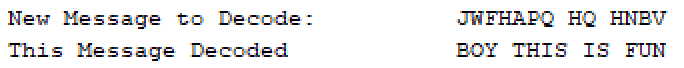
In the above example the message you stole had every letter in the alphabet. If you ended up stealing a message that didn’t have the whole alphabet then you won’t be able to decode every message as you won’t have the entire mapping sequence.
For example if this is what you stole:
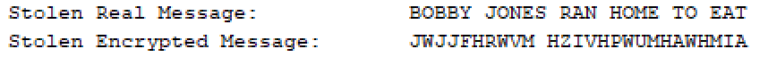
Then when you try to decode another message, some letters will be missing

Write a program that can decode the rebel messages as best as possible.
The input will be from a file.
- The first line will the Real Stolen Message
- The second line will be the Encrypted Stolen Message
- The third line will be the Message you want to decode
- All Messages will be entirely upper case and will have no punctuation other than spaces
The output for this program will be to the screen
- If a letter can’t be decoded replace it with a ‘.’
IB Computer Science Question 3
A message is encrypted in the following way:
- Put a secret password (case sensitive) at the start of the message
- Split the message into two halves, with the second half having equal or one more than the number of characters than the first half. (Spaces and other characters need to be included)
- Reverse the second half of the message
- Insert that reversed string into the first half by alternating characters from the first half, always starting with the first character of the second half. This is known as a fold.
- Continue splitting and folding a random number of times
Consider the following example
- Message: I really am a snake
- Secret Code: Rogers
Here is the first fold occurring
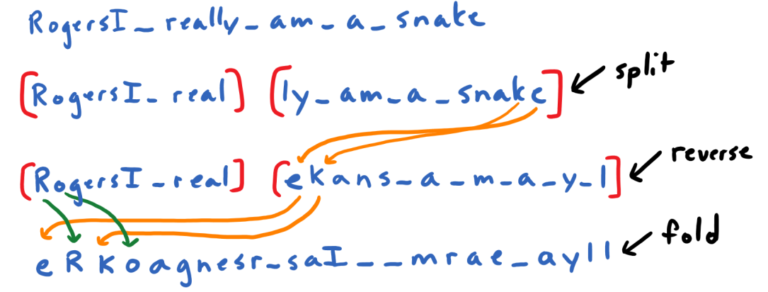
Here is the message folded 6 times

You can decode these messages as long as you know the secret code. You don’t need to know how many times it was folded to decrypt. You just have to unfold until you find the secret code at the start.
Example: If you know the secret code is Albert Einstein

Write the following programs:
- The encryption program – Takes a message and a secret code and encrypts it with the above algorithm.
- The decryption program – Takes a message that was encoded with the above algorithm and then decodes it to the real message.
I will be testing the encryption program with keyboard input
- First input should be the secret password
- Second input should be the message to encode.
- Third input should be the number of times to fold the message
I will be testing the decryption program with a text file that has
- Line 1 being the secret password and a number representing the number of sentences to decode. These will be separated by a comma.
- The remaining lines will be the encoded sentences. Each sentence will have a pair of < > surrounding the encrypted message to ensure that trailing spaces are included.
The output for both programs can be to the screen
- Your encryption code should surround the encrypted message with a pair of < > symbols to make sure that the leading or trailing spaces are included.
- You do NOT need to show the folding / unfolding process. Only the final answers are necessary.
Sample Input and Output Encryption
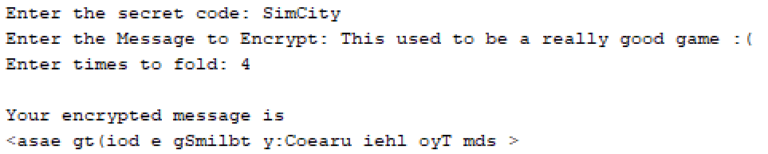
Sample Input / Output Decryption
IB Computer Science Question 4
In this particular program you are going to store data on a DVD ROM
The input file (DVDromIN.txt) will contain 5 lines of data. Each line contains information about 1 DVD ROM. Each line will contain the following information: The first integer will represent the amount of storage space on the DVD ROM, the second integer will represent how many files you will try to store on the DVD, each subsequent integer will represent the sizes of those files. All data is separated by a single space.
The output file (DVDromOUT.txt) will contain 5 lines of data, corresponding to each line of the input file. Each line will display whether or not ALL the files will be able to fit on the DVD followed by the files that are going to fit. Files are written to the DVD in the order they are listed in the input file. If a file doesn’t fit, it is skipped and the next file is checked to see if it will fit.
Files are stored on the DVD ROM in the order listed in the input file
Sample Input / Sample Output
700 4 500 300 300 100 / NO 500 100
700 5 200 75 240 750 420 / NO 200 75 240
650 3 100 100 400 / YES 100 100 400
650 1 750 /NO
700 3 100 200 400 / YES 100 200 400
IB Computer Science Question 5
Pig Latin is a made up language where you take the first letter of a word and move it to the end of the word and add an “ay” to the end

The input file (pigIN.txt) will contain 5 sentances, 1 per line, with each word separate by spaces, no punctuation.
The output file (pigOUT.txt) will be those sentances translated into Pig Latin
IB Computer Science Question 6
A little kid has been given directions on how to get to school from his house. Unfortunately he lost the paper that tells him how to get home from school. Being that you are such a nice person, you are going to write a program to help him.
Suppose his mother gave him a note that said the following:

You need to write him a note back that said the following:

Input and Output for this program will be from a file and to a file.
All text will be on separate lines.
All text will be all uppercase.
Looking to Learn More about Computer Science and Coding?
Check out our programing in python courses that focus on high school level coding.
These courses are complete with interactive coding lessons, teacher led videos, and more practice questions with complete solutions
Return To International Baccalaureate Computer Science Main Page
